- cybersecurity
Zero Trust for Beginners: Why "Trust No One" is Your Best Defense

Have you ever had that sinking feeling when you receive an email saying, "New login detected on your account"?
For a split second, panic sets in. You scramble to check your bank app, your social media, or your university portal. In today's digital world, that feeling is becoming all too common. Whether you are a college student juggling assignments on a coffee shop Wi-Fi or an aspiring Information Security (InfoSec) professional looking for your first big break, the digital landscape feels like a minefield.
For decades, we relied on a simple security model: keep the bad guys out and trust the good guys inside. But in an era of remote learning, cloud apps, and sophisticated hackers, that model has failed.
Enter Zero Trust.
It sounds intense—maybe even a little paranoid—but Zero Trust is the most important concept in modern cybersecurity. It is not just a piece of software you buy; it is a mindset. It is the philosophy that is saving companies, universities, and individuals from catastrophic data breaches.
In this guide, we are going to strip away the complex jargon and explain Zero Trust in plain English. We will look at why the old ways failed, how Zero Trust works, and how you can apply it to your own digital life.
The Old World: Why the "Dorm Room" Model Failed
To understand why Zero Trust is the future, we have to look at the past.
For a long time, digital security was designed like a traditional college dormitory.
Imagine a dorm building. It has a heavy lock on the front door, maybe even a security guard. This is the Perimeter.
Outside: Strangers, thieves, and danger. (Untrusted)
Inside: Students, friends, and roommates. (Trusted)
In this old model, once you swiped your ID card and got past the front door, you were considered "safe." Inside the dorm, people often left their doors unlocked. They left laptops on common room tables. They shared snacks freely. The system assumed that because you were inside the building, you belonged there.
The Problem with the Dorm Model
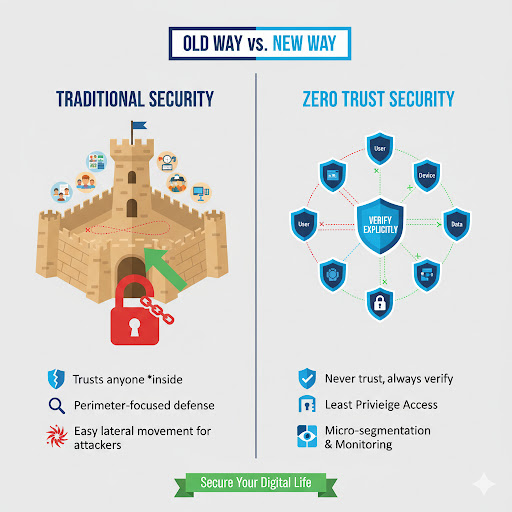
This "Castle and Moat" approach works fine—until someone steals a student ID.
If a hacker finds a lost ID card (or steals a password via phishing), they can walk right through the front door. Once inside, the security guard ignores them. The hacker can now walk into any room, steal any laptop, and access any data because the system stops checking credentials after the front door.
In technical terms, this is called Lateral Movement. It is when a hacker breaches one device and then jumps from computer to computer until they find the valuable data.
The New World: Enter the "Zero Trust" Library
Zero Trust completely destroys the old model. It assumes that the "dorm" is already compromised. It assumes a stranger might already be inside.
Let’s change the analogy to a High-Security University Library.
In a Zero Trust Library, showing your ID at the front door is just step one.
You want to enter the library? Check ID.
You want to go to the Science Section? Check ID again.
You want to access the Rare Book Room? Check ID, check class schedule, and check if your professor approved it.
You want to check out a book? Scan ID and verify your fingerprint.
This approach is based on a simple, non-negotiable motto: "Never Trust, Always Verify."
It doesn't matter if you are the Dean of the University or a first-year student. The system validates you every single time you try to touch a new resource. It ensures that even if a hacker steals your ID card, they can't get very far.
The Three Pillars of Zero Trust
You don't need to be a coding wizard to understand the architecture of Zero Trust. It stands on three massive pillars. If you are studying for a career in InfoSec, memorize these—they will be in your job interviews.
1. Verify Explicitly (The "Who, What, Where" Check)
In the old days, a password was enough. In Zero Trust, a password is just the beginning. The system looks at the context of your request.
Imagine you are logging into your school portal to submit an assignment.
Old Way: You type your password. Access Granted.
Zero Trust Way: The system analyzes the request.
Who is this? (User ID)
What device are they using? (Is it your usual laptop? Is the antivirus updated?)
Where are they? (Are you on campus, or is this login coming from Russia?)
When is it? (Is it 2 PM or 3 AM?)
If you try to log in from an unknown iPad in a different country at 3 AM, the system will block you—even if the password is correct. This is Explicit Verification.
2. Least Privilege (The "Need-to-Know" Basis)
This is the most critical concept for students and interns. Least Privilege means giving a user the bare minimum access they need to do their job—and nothing more.
Think about a group project on Google Drive.
You have the main "Final Report" doc.
You invite your group members to edit it.
Do you also give them access to your personal finance folder? No.
Do you give them access to your private photos? No.
You give them access to one file for one week. That is Least Privilege. In a company, this ensures that if a marketing intern gets hacked, the hackers can't access the CEO’s financial records. It limits the "Blast Radius" of an attack.
3. Assume Breach (The Paranoid Mindset)
This pillar is a psychological shift. It is the pessimist’s guide to security.
In traditional security, IT teams hope for the best. In Zero Trust, IT teams assume the worst. They operate under the assumption that a hacker is already inside the network, hiding in the shadows.
Because they assume a breach has happened, they:
Encrypt all data (make it unreadable without a key).
Segment the network (break it into tiny, locked zones).
Constantly monitor traffic for weird behavior.